![]() Secure Global Desktop 4.40 Administration Guide
> Security
> User Prompts and X.509 Certificates
Secure Global Desktop 4.40 Administration Guide
> Security
> User Prompts and X.509 Certificates
When users log in to an SGD server that has an X.509 certificate, the SGD Client
validates the certificate before proceeding. If the certificate is valid and users have
agreed to the initial connection to SGD, the host name and
the fingerprint of the certificate are added to the hostsvisited file on the client device. The hostsvisited file is
stored in the same location as the user's profile cache.
However, if there are problems with the X.509 certificate, for example because the issuer of the certificate is unknown or the certificate has expired, users see a certificate warning message and they are prompted to accept or reject the certificate. This is a potential security risk. How certificate warnings are handled depends on whether or not SGD security services are enabled.
Note Users see prompts about security certificates before agreeing to trust the initial connection to SGD.
When SGD security services are disabled and users see a security warning message about an X.509 certificate, the warning message allows users to view the certificate details before deciding to accept or reject the certificate.
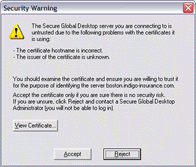
If users accept the certificate and they agree to the connection to the server, the host name and fingerprint of the certificate are added to the hostsvisited file on the client
device. The certificate is cached for the lifetime of the user session. When users next log in, they are not prompted about the certificate.
If users reject the certificate, the connection to SGD is terminated and the certificate details are not
added to the hostsvisited file. When users next log in, they are prompted about the certificate.
If users have previously accepted a certificate, or if the only error with the certificate is that the issuer is unknown, then users are not prompted about the certificate.
When SGD security services are enabled and users see a security warning message about an X.509 certificate, the warning message allows users to view the certificate details before deciding to accept the certificate permanently or temporarily, or to reject the certificate.
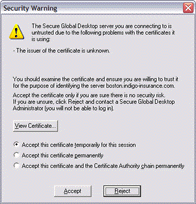
If users accept the certificate temporarily and they agree to the connection to the server, the host name and fingerprint of the certificate are
added to the hostsvisited file on the client device. The certificate is cached for the lifetime of the user session. When users
next log in, they are prompted about the certificate.
If users accept the certificate permanently and they agree to the connection to the server, the hostname and fingerprint of the certificate are added to thehostsvisited file
on the client device. The certificate is also added to the certstore.pem file on the client device.
The certstore.pem file is stored in the same location as the user's client profile
cache. Users can choose to accept just the certificate or the certificate and its chain.
When users next log in, they are not prompted about the certificate.
If users reject the certificate, the connection to SGD is terminated and no certificate details are added to the
hostsvisited file. When users next log in, they are prompted about the certificate.
In a default installation, SGD supports X.509 certificates that have been signed by a number of Certificate Authorities.
You can use any other type of Base 64-encoded PEM-format X.509 certificate. However, these certificates cannot be validated unless you install the Certificate Authority (CA) certificate (or root certificate) that was used to sign that certificate. If you do not install the CA certificate, users see an issuer unknown error and are prompted to accept or reject the certificate.
If you are using a secure (HTTPS) web server, users are prompted to accept the web server's certificate if the root certificate has not been imported into the web browser's keystore. To allow the web server certificate to be validated without prompting the user, import the root certificate into the user's web browser using the browser's tools for doing this.
If you are using Java™ technology with a secure web server, the Java Plug-in might also prompt users to accept the web server's certificate. This depends on the configuration in the Java Control Panel. By default, the Plug-in is configured to use the certificates in the browser keystore. If the Plug-in is not configured to do this, you might have to import the root certificate using the Java Control Panel.
Copyright © 1997-2007 Sun Microsystems, Inc. All rights reserved.