 Secure Global Desktop 4.31 Administration Guide
> Security
> Using Secure Global Desktop with firewalls
Secure Global Desktop 4.31 Administration Guide
> Security
> Using Secure Global Desktop with firewalls
Using Secure Global Desktop with firewalls
Problem
You have a number of firewalls protecting various parts of your
network and you want to use Secure Global Desktop.
Solution
Configure your firewalls to allow packets to be sent between client
devices used for Secure Global Desktop and your Secure Global Desktop
servers, and between your Secure Global Desktop servers and your
application servers. Ensure that the DNS names of web servers and
Secure Global Desktop servers are configured correctly for the clients
you want to use to log in to Secure Global Desktop.
Using Secure Global Desktop security allows you to securely traverse firewalls.
Case study
Indigo Insurance currently uses two firewalls:
- An application server firewall surrounding all application servers.
- An external firewall between the Internet and the intranet.
Indigo Insurance is installing an array of Secure Global Desktop
servers and wants to configure the firewalls to ensure access by
client devices, both inside and outside the external firewall, to any
application server, using Secure Global Desktop. Also, Indigo Insurance
wants to protect the Secure Global Desktop servers behind their own
firewall. Each host on which a Secure Global Desktop server is
installed has a single network card.
Here's a diagram of the intended network structure:
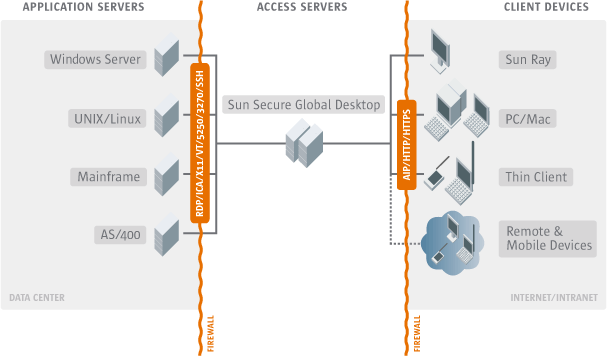
Solution
- The external firewall and the Secure Global Desktop firewall must
both allow network traffic for the web server and Secure Global Desktop
server for all array members.
- For the web server:
- 80/tcp if you use an HTTP web server.
- 443/tcp if you use a secure (HTTPS) web server.
- For the Secure Global Desktop server:
- 3144/tcp if standard connections are available.
- 5307/tcp if secure connections are available.
Typically, you would open either ports 80/tcp and
3144/tcp or ports 443/tcp and 5307/tcp.
You should close port 5427/tcp. This is used for essential network
traffic between Secure Global Desktop servers only.
You can expose only a subset of Secure Global Desktop array members
on the Internet. However, if users typically log in to
Secure Global Desktop from both inside and outside the external
firewall then they may be unable to resume some applications when
logging in from the Internet.
- The application server firewall must allow network traffic between
the Secure Global Desktop server and the application server for
all array members. The ports you need to open depend
on the types of application you're using.
- 22/tcp for X and character applications using SSH.
- 23/tcp for Windows, X and character
applications using telnet.
- 512/tcp for X applications using rexec.
- 3389/tcp for Windows applications configured to
use Windows Terminal Services.
- 6010/tcp and above for X applications (the
number of ports to open depends on the number of simultaneous
emulator sessions the Secure Global Desktop server will support).
- To support printing, the application server firewall must allow
network traffic between all array members and
the application server on port 515/tcp.
- The application server firewall should deny connections to ports
3144/tcp, 5307/tcp and 5427/tcp: these are not used for network
traffic to and from application servers.
- Systems may be known by different names inside and outside
firewalls. For each Secure Global Desktop array member:
- Find out the DNS name to use inside the Secure Global Desktop
firewall for the Secure Global Desktop host, and the DNS name to use
outside the Secure Global Desktop firewall for the
Secure Global Desktop host. (The names may be the same.)
- Configure the web server to bind to the DNS name used
inside the Secure Global Desktop firewall (this is
the DNS name the web server binds to when it starts). Consult your
web server documentation for help.
- Configure the Secure Global Desktop server with the name used
outside the Secure Global Desktop firewall (this is
the DNS name the client device uses to contact the web server). You
configure this name in Array Manager, in the array member's
General properties.
Next steps
Copyright © 1997-2007 Sun Microsystems, Inc. All rights reserved.
![]() Secure Global Desktop 4.31 Administration Guide
> Security
> Using Secure Global Desktop with firewalls
Secure Global Desktop 4.31 Administration Guide
> Security
> Using Secure Global Desktop with firewalls